Recommended Services
Supported Scripts
WordPress
Hubspot
Joomla
Drupal
Wix
Shopify
Magento
Typeo3
Endpoint Detection and Response
ENDPOINT DETECTION AND RESPONSE
Understanding the complete context of an attack can help you grasp how hackers are attempting to infiltrate your network. It's crucial to swiftly pinpoint attacks through detailed root-cause analysis for effective remediation strategies.

GET REAL-TIME EDR FORENSICS
Threat Visualizations for Attack Velocities
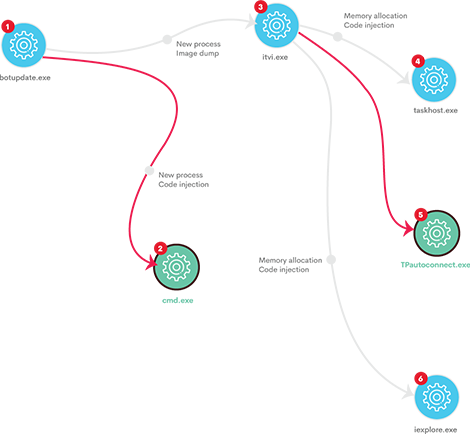
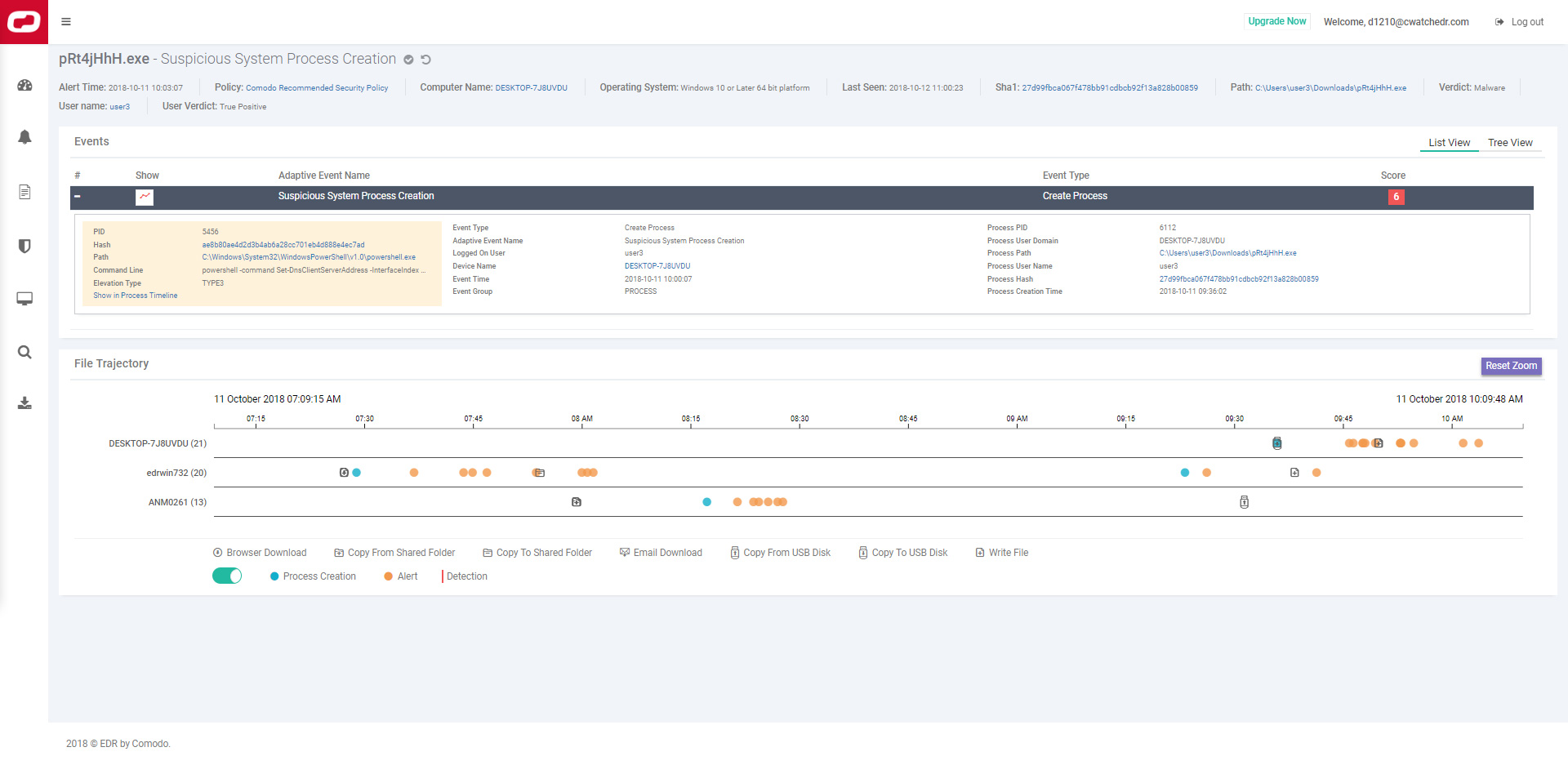
We combine attack paths with file movement and process hierarchy to quickly address any issues, all visible on your dashboard. Process-based events are shown in a tree-view structure to help analysts understand process behavior. Device trajectory data for analyzing attack paths is provided on separate screens, allowing for detailed device investigation.
Feature Capabilities
Visualizations of an attack chain
To aid analysts in understanding process behaviour, process-based events are displayed in a tree-view structure.
Investigating an incident
Analysts can conduct queries on the event search screen to retrieve any detail down to the base-event level of granularity.
Threat Intelligence Analyzers Valkyrie
Performs a variety of run-time behavioural analyses on unfamiliar files to rapidly and automatically determine if they are safe or dangerous.
Recommendations for Security
The Security Policy is included with every EDR licence and can be altered to suit your specific requirements.
Structure Based on the Cloud
Our nimble agent to gather data and delve down into incidents with fundamental event-level specificity.
Support for auto-containment
operates automatically from a proprietary virtual container that prevents attacks from accessing the resources or user data of the host system.
Alerting for Suspicious Activity
Receive alerts for actions including fileless assaults, sophisticated persistent threats, and attempts at privilege escalation.
Malware detection without files
Some malware assaults RAM instead of executing a file. These dangers can be recognised by Techsagepro EDR even before they manifest.