Recommended Services
Supported Scripts
WordPress
Hubspot
Joomla
Drupal
Wix
Shopify
Magento
Typeo3
Endpoint Manager
ENDPOINT DETECTION AND RESPONSE
By recognising apps, comprehending vulnerabilities, and applying updates, practice cyber hygiene to limit the attack surface.
REDUCE YOUR ATTACK SURFACE
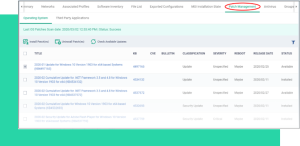
Discover, Audit, and Compliance—all-in-one
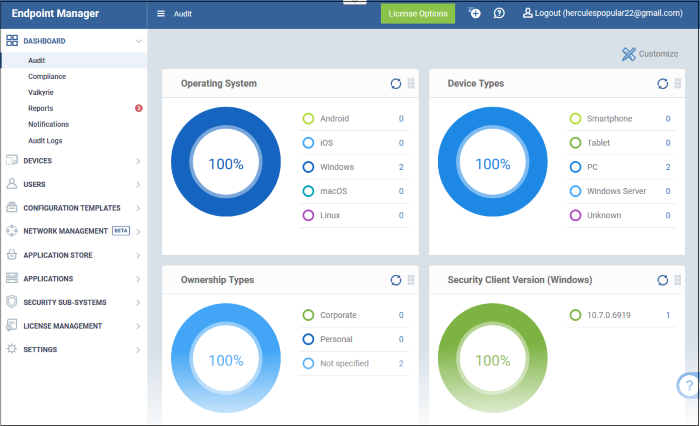
The dashboard displays information in real-time regarding the connection status, operating system, and security posture of every device registered with Endpoint Manager. You may view threat results, receive notifications, and create reports using the dashboard.
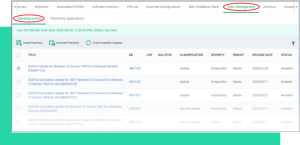
Discover, Audit, and Compliance—all-in-one
The dashboard displays information in real-time regarding the connection status, operating system, and security posture of every device registered with Endpoint Manager. You may view threat results, receive notifications, and create reports using the dashboard.
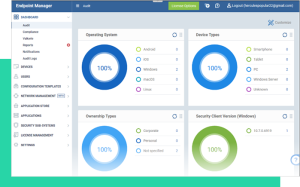
Compliance—all-in-one
The dashboard displays information in real-time regarding the connection status, operating system, and security posture of every device registered with Endpoint Manager. You may view threat results, receive notifications, and create reports using the dashboard.
Feature Capabilities
Setup any Major OS
Manage the operating system on your device to keep Linux, Windows, or Mac systems optimal, safe, and secure.
Recommended Security Policy
You can customise a device’s network access rights, general security policy, and antivirus scan schedule settings using each profile.
Patch Control
One comprehensive list allows you to manually or automatically update your devices, operating system, and third-party software.
Network Management
Devices that are managed and unmanaged will both be found by the scan. If a scan turns up any new devices, you may set EM to notify you.
Structure Based on the Cloud
Our nimble agent to gather data and delve down into incidents with fundamental event-level specificity.
Alerts and Notifications
To track certain activities and send out alerts when their requirements are met, create procedures and monitors.
Valkyrie Verdicting Engine
performs a variety of run-time behavioural analyses on unfamiliar files to rapidly and automatically determine if they are safe or dangerous.
Support for auto-containment
operates automatically from a proprietary virtual container that prevents attacks from accessing the resources or user data of the host system.
