Recommended Services
Supported Scripts
WordPress
Hubspot
Joomla
Drupal
Wix
Shopify
Magento
Typeo3
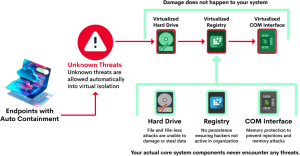
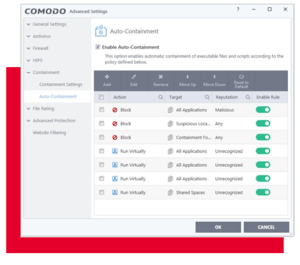
Auto containment
IMMEDIATELY BLOCK ZERO-DAY MALWARE
We offer auto containment services that prevent unknown threats from damaging endpoints in real-time. Our Techsagepro Threat Research Labs (CTRL) and Valkyrie file safety assessment service, along with our SaaS administration console, endpoint client agents, and other service delivery channels, are all part of this solution.
Get Rid of Threats That Avoid Detection
Unrecognized executable files requiring runtime capabilities are automatically initiated within a virtual container. This container is isolated from user data on endpoints and resources of the host system.
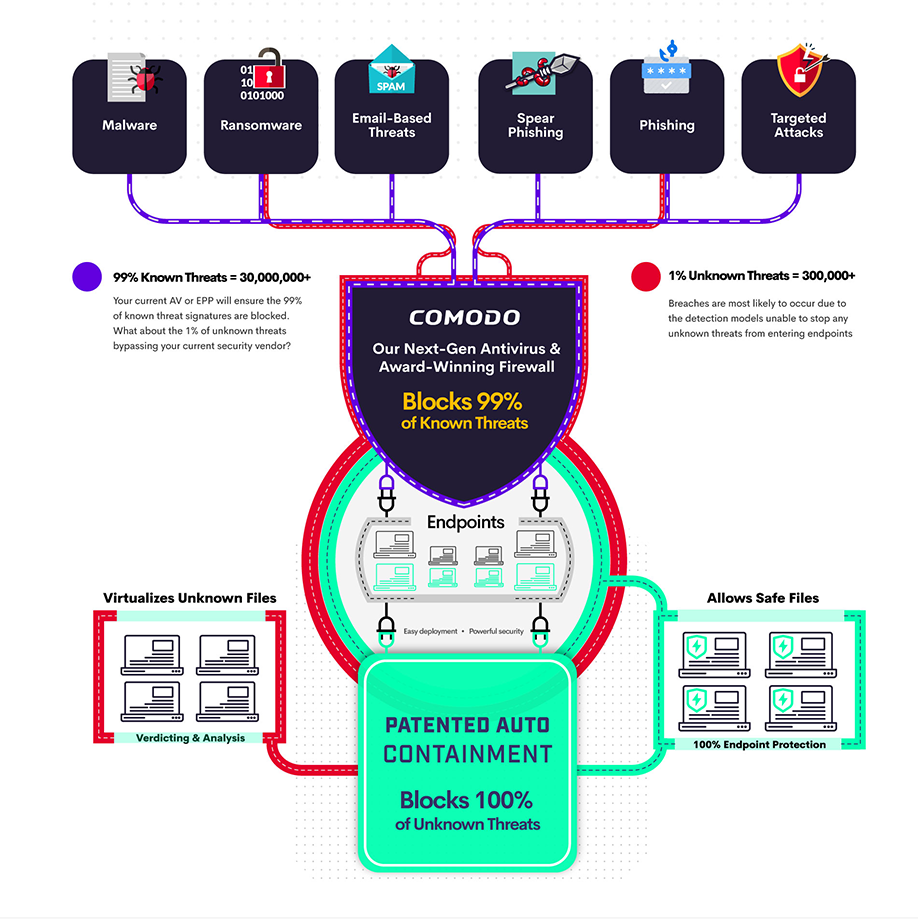
IMMEDIATELY PROTECTS FINISH POINTS FROM DAMAGE AND THREATS
Learn more about the dark web.
Access specialized threat intelligence feeds to alert or prevent potential security breaches from both internal and external sources. For broader protection, combine your organization's internal intelligence with Techsagepro's Dragon Enterprise. Fully integrate Valkyrie to conduct MD5 hash submission checks during process execution.
Patented Auto Containment
Denies write access privileges to all unknown-unknown threats, instantly stopping all unknown threats.
NGAV & Award-winning Firewall
Real-world antivirus software with strong detection, eradication, and quarantine capabilities
Fileless Malware Protection
protection from fileless malware payloads that evade conventional antivirus software
Analyzer of Virus Scope Behavior
Monitors all processes for unusual activity in order to spot any acts that could be dangerous before they take place.
Default Security Profiles
Keep out any incoming threats and watch out for any suspicious outgoing threats.
Analysis of malicious scripts
Continuous operating system activity monitoring to find intrusions before any trespassing may take place
Threat Intelligence Analyzers Valkyrie
Real-time static and dynamic searches of the cloud, the deep web, and the black web for potential risks to your company
Cloud-based Updates
To guarantee security and the best user experience, fresh malware signatures are regularly supplied through the cloud.