Recommended Services
Supported Scripts
WordPress
Hubspot
Joomla
Drupal
Wix
Shopify
Magento
Typeo3
Managed Detection Response
MANAGED
DETECTION
AND RESPONSE
Your vulnerabilities stem from a lack of necessary tools, systems, and possibly the technology needed to support all these advancements. Strengthen your capabilities with our unified managed solution, covering endpoint management, exploit protection, and advanced threat hunting.
REMEDIATION AND SOC INVESTIGATION
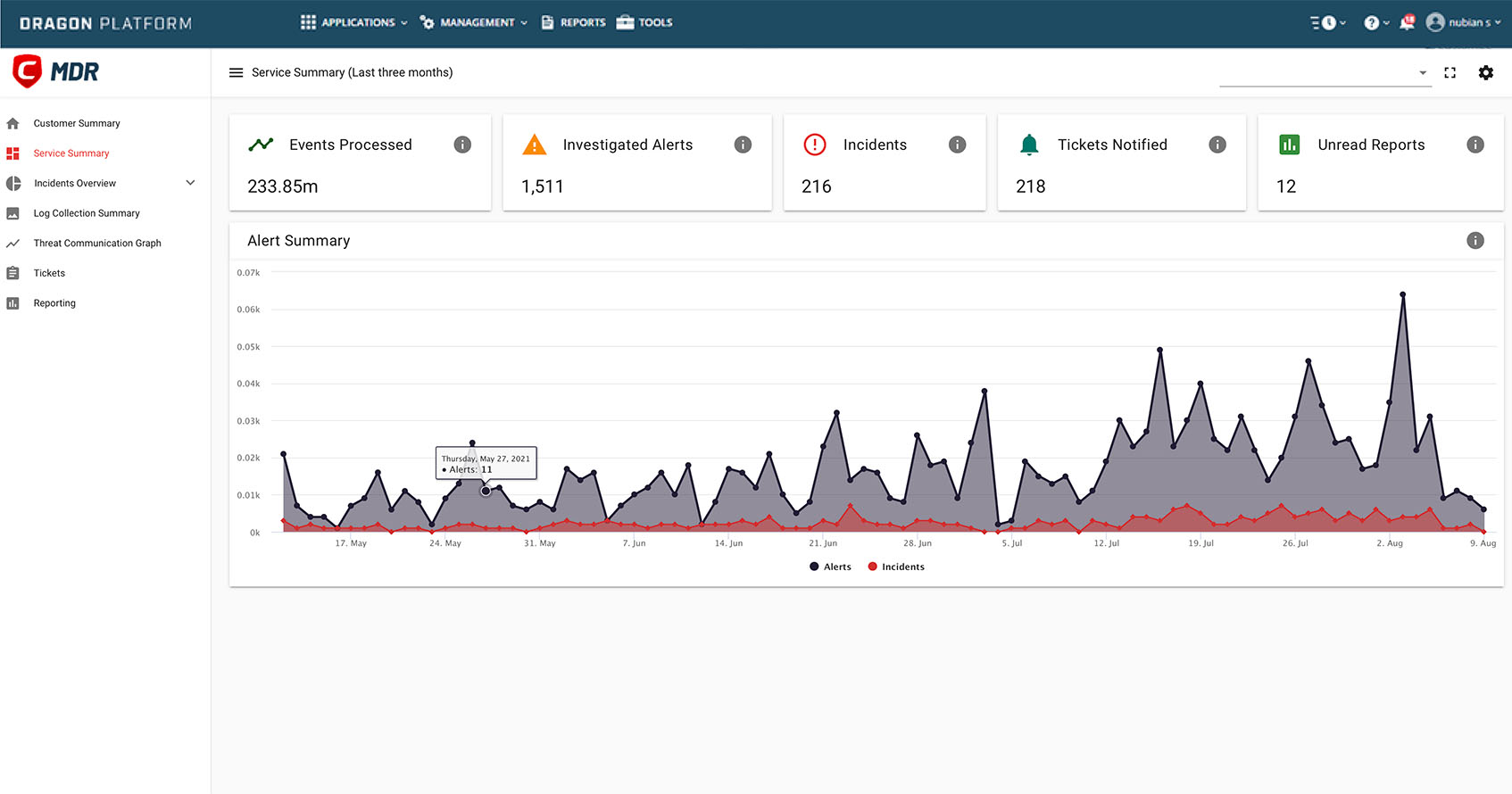
- 24•7•365 Continuous Monitoring
- Reports and Managed Response.
- Proactive APT Threat Hunting
- Integrations of threat intelligence
 Employ a team of expert forensic analysts who are accessible 24/7 to conduct comprehensive investigations. Receive a detailed timeline of the attack's actions through endpoint forensics, including analyses of MFT$, Windows Event Logs, the Registry, Web History, and other relevant artifacts. Additionally, benefit from Threat Neutralization support during Incident Response to prevent any potential breaches.
Employ a team of expert forensic analysts who are accessible 24/7 to conduct comprehensive investigations. Receive a detailed timeline of the attack's actions through endpoint forensics, including analyses of MFT$, Windows Event Logs, the Registry, Web History, and other relevant artifacts. Additionally, benefit from Threat Neutralization support during Incident Response to prevent any potential breaches.

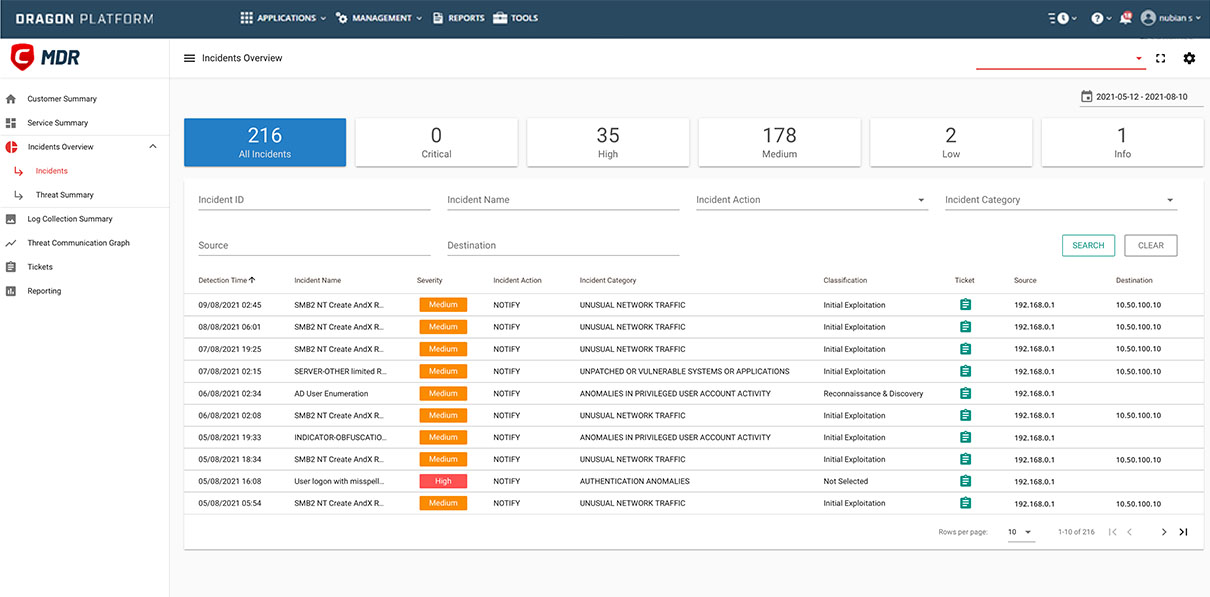
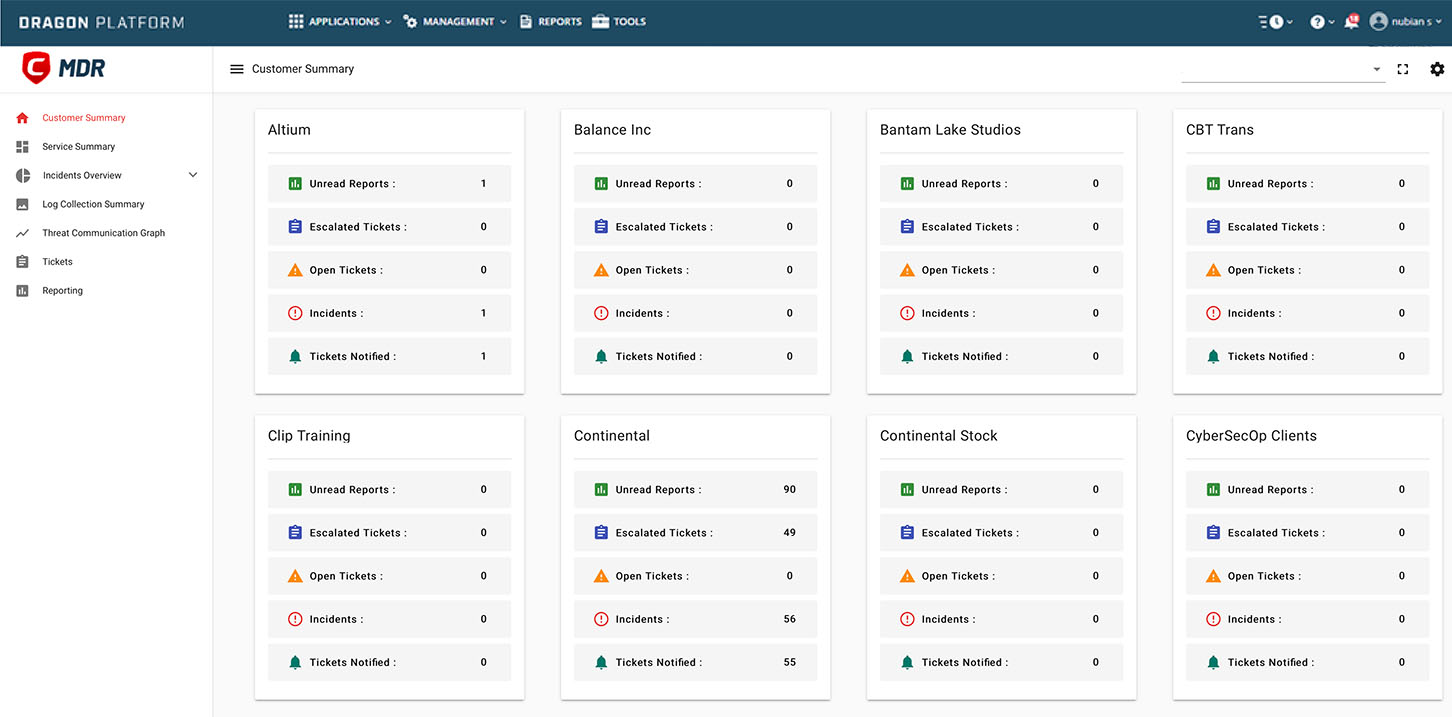
Analysts will monitor your system for potential hazards and alerts. They'll prioritize these alarms and events, notifying you through the Dragon Enterprise Platform if there's any suspicious activity indicating a compromise. Receive detailed notifications about the presence of attackers, hazardous software, and guidance on distinguishing false alarms.
A dedicated team of cybersecurity experts will conduct continuous professional threat hunting across your organization. They'll meticulously examine logs to detect any unusual or suspicious behavior. By establishing a baseline for normal activity, we'll promptly notify you if there's any deviation from the expected behavior in your environment.

To enhance your understanding of the dark web, acquire specialized threat intelligence feeds from both internal and external sources. These feeds can alert you to potential compromise indicators and help prevent security breaches. For additional protection, integrate your company's internal intelligence with Techsagepro's Dragon Enterprise. Ensure full Valkyrie integration for MD5 hash submission checks during process execution for comprehensive security measures.
Feature Capabilities
Managed Coverage Throughout the Day
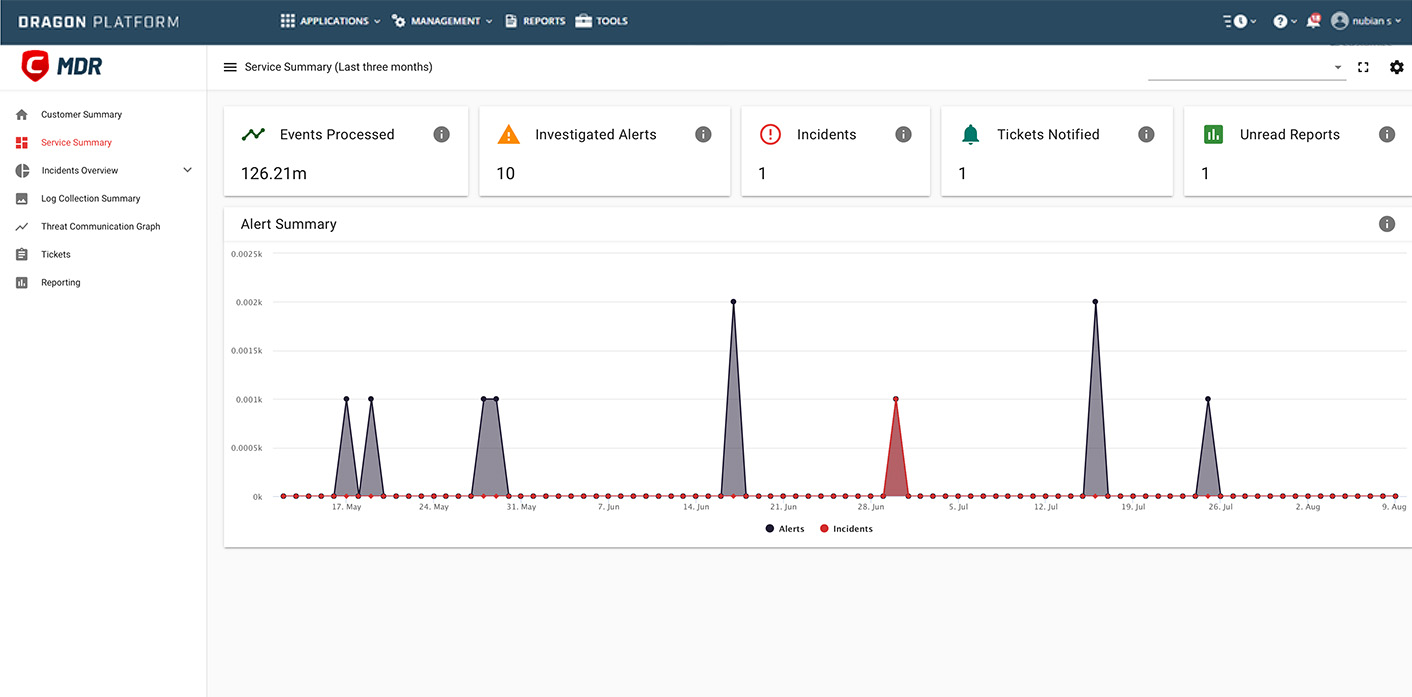
Our professionals vigilantly monitor changes to your environment round the clock, regardless of your time zone or location, ensuring comprehensive coverage 24/7.
SOC Team Supplements
Delegate day-to-day operations and threat hunting tasks to our MDR (Managed Detection and Response) experts to allow your staff to concentrate on your organization's demands without distractions.
Reduce alerts and Intelligence
Receive alerts for various actions, such as fileless attacks, sophisticated persistent threats, and attempts at privilege escalation, to stay informed and respond effectively to potential security threats.
Investigating an incident
Analysts have the capability to perform detailed queries on the event search screen, allowing them to retrieve specific information down to the most granular level of individual base events.
Structure Based on the Cloud
Our agile agent efficiently collects data and thoroughly investigates incidents, with a focus on fundamental event-level details.
Verdicting Engine for Valkyrie
Conducts a range of behavioral analyses in real-time on unfamiliar files to quickly and automatically assess whether they pose a threat or are safe to use.
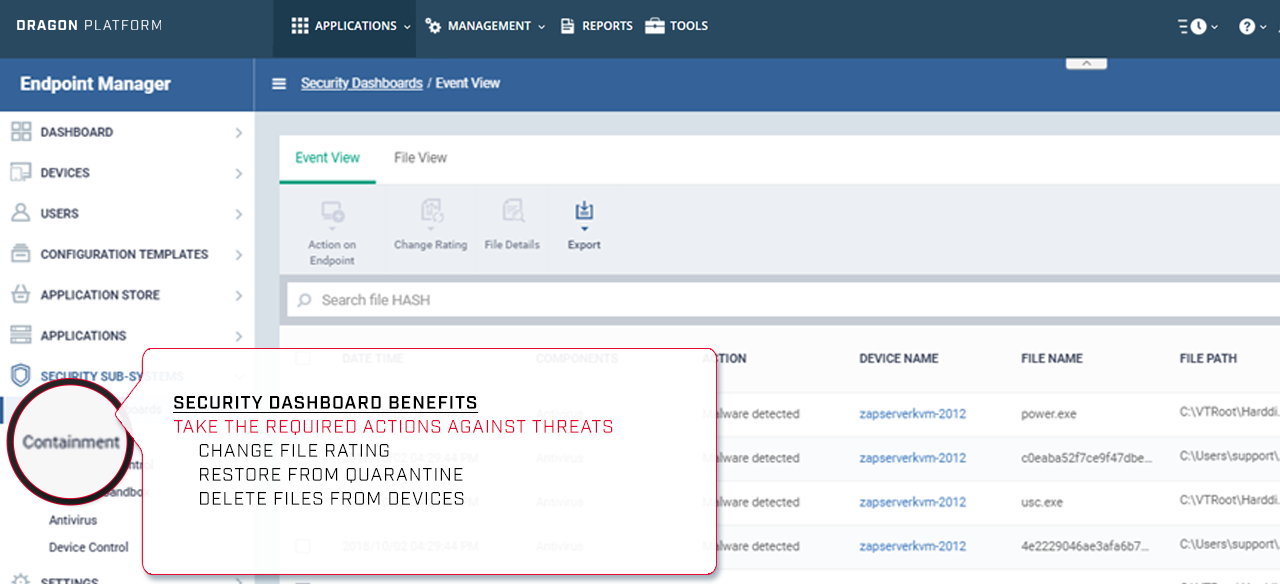
Enhanced auto-containment
Operates autonomously within a specialized virtual container, proprietary to our system, which effectively blocks attacks from accessing the resources or user data of the host system.
